Palo Alto Firewall Best Practices
712020 The Best Practice Assessment is a free tool we have developed specifically to help you configure your firewall correctly as recommended and set for risk prevention. 4222020 Best Practice Assessment 99 of firewall breaches through 2023 will be due to firewall misconfigurations not firewall flaws according to Gartner research1 Companies typically implement basic capabilities and postpone setting up many features that maximize protection.
Pro Tips Unknown Applications Knowledge Base Palo Alto Networks
Follow the best practices PAN-OS 81 90 91 100 to secure your network from Layer 4 and Layer 7 evasions to ensure reliable content identification and analysis.

Palo alto firewall best practices. We put our five years of experience in designing implementing supporting and managing Palo Alto Networks solutions together and wrote this guide to share our best practices to secure an enterprise network using a Palo Alto Networks Next-Generation FireWalls. 3192021 Isolate the Management Network. Best Practice Assessment BPA Tool The BPA for next-generation firewalls and Panorama evaluates a devices configuration by measuring the adoption of capabilities validating whether the policies adhere to best practices and providing recommendations and instructions for how to remediate failed best practice checks.
The Palo Alto Networks Best Practice Assessment BPA measures your usage of our Next-Generation Firewall and Panorama security management capabilities across your deployment enabling you to make adjustments that maximize your return on investment and strengthen security. All fields are required registrationForm First_Name__c Last_Name__c Business_Email newPassword Company Job_Level__c Job. Introducing the all-new Improving Security Posture and Hardening PAN-OS Firewalls.
All Palo Alto Networks firewalls provide an out-of-band management MGT port that you can use to perform firewall administration functions. 3192021 Use decryption on a firewall to prevent malicious content from entering your network or sensitive content from leaving your network concealed as encrypted or tunneled traffic. Specifically make sure that you implement the best practices for TCP settings.
Attach a best practice decryption profile to the decryption policy rule to ensure that you are blocking vulnerable SSLTLS versions such as TLS 10 and SSLv3 and rejecting sessions using weak encryption algorithms such as RC4 and 3DES and weak authentication algorithms such as. In short the Palo Alto Networks Best Practices Tool can give you a clearer picture of how your security appliance is utilizing the features that Palo Alto offers. If you own Palo Alto Networks Next-Generation Firewalls and manage software updates including Dynamic Updates learn best practices and recommendations to ensure smooth deployment of weekly content from Palo Alto Networks.
Share Threat Intelligence with Palo Alto Networks Permit the firewall to periodically. And our best practice. Firewall Hardening Best Practices for Palo Alto Networks.
It gives a taste of the new course by teaching a full module. 672020 Besides our own it incorporates security best practices recommended by Palo Alto Networks BPA. On Tuesday 27th of October 2020 we run this training workshop for Palo Alto Networks.
As well as the Center for Internet Security CIS Controls. Best Practices for Deploying Content Updates. Implementing a central management system to view and preside over your many firewall deployments can give you full visibility into your entire network and help you to orchestrate detection and protection based on real-time intelligence.
A firewall is only as good as the features that you take advantage of. The BPA quickly identifies critical security controls for your organization to focus on. Much of the time its not obvious where the gaps are in the use of those features.
Whether youre looking for the best way to secure administrative access to your next-gen firewalls and Panorama create best practice security policy to safely enable application access at the internet gateway and the data center or learn the best way roll out a decryption policy to prevent threats from sneaking into your network you will find the guidance you need here in our best practice documentation. Contact us or give us a call 353 1 5241014 1 650 407-1995 - We are a Palo Alto Networks Certified Professional Service Provider CPSP and the Next-Generation Security. Network Security Best Practices for Palo Alto Networks Next-Generation FireWalls.
Exclude certain web traffic from decryption Use URL categories to make decryption exceptions especially if you want to exclude certain types of sites from decryption because of privacy concerns for example financial-services and health-and-medicine sites. Some of the key best practices for secure firewall administration we will look at in this article include the following. This chapter highlights the Palo Alto Networks methodology for implementing Panorama and our.
Alternatively you can use the MGT port for initial configuration and then configure a data port for management access to the firewall. This page will provide more information about this feature. 3232021 WildFire Best Practices.
Follow the Best Practices for Securing Your Network from Layer 4 and Layer 7 Evasions. Targeting decryption and phasing it in based on URL categories are also Decryption best practices.
Security Policy Fundamentals Knowledge Base Palo Alto Networks
Best Practices For Deploying Content Updates Knowledge Base Palo Alto Networks
Security Policy Fundamentals Knowledge Base Palo Alto Networks
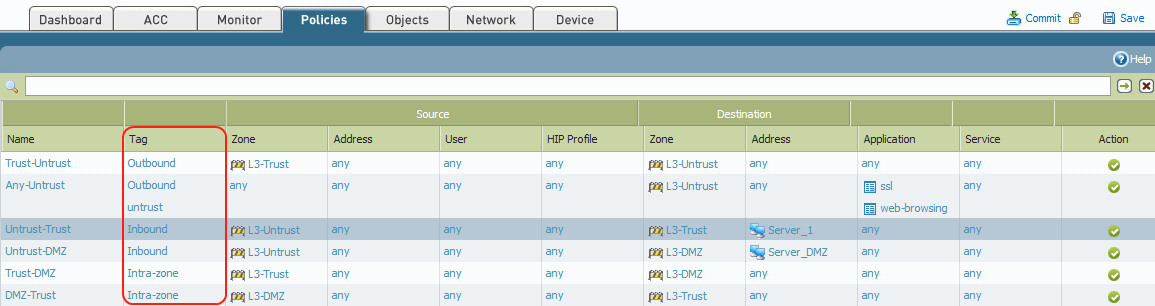 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks
 How To Protect The Datacenter Palo Alto Networks Firewall Concepts Training Series Youtube
How To Protect The Datacenter Palo Alto Networks Firewall Concepts Training Series Youtube
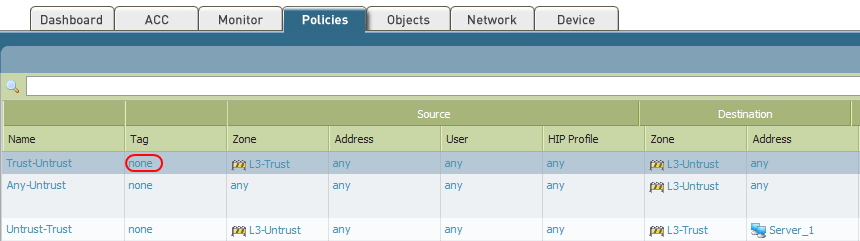 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
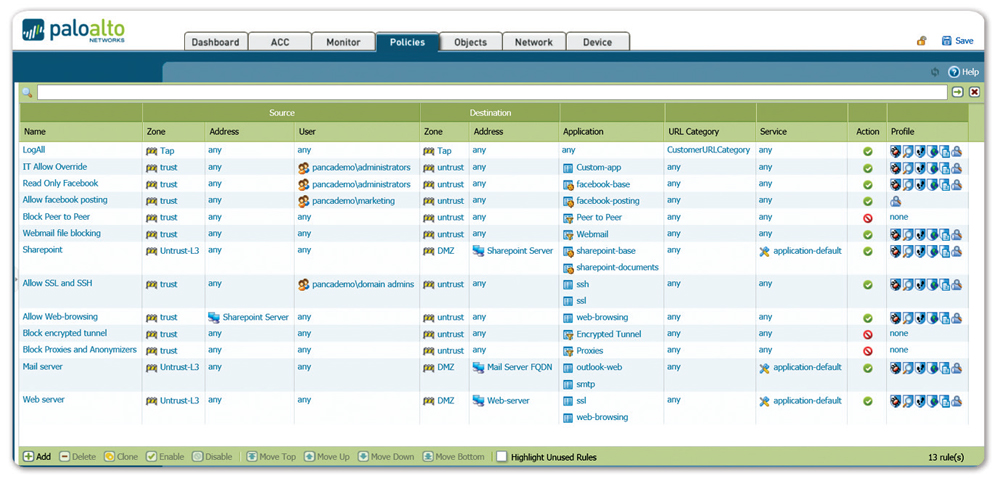 Palo Alto Networks Enterprise Firewall Pa 5020 Paloguard Com
Palo Alto Networks Enterprise Firewall Pa 5020 Paloguard Com
Tips Tricks Highlight Unused Rules Knowledge Base Palo Alto Networks
How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks
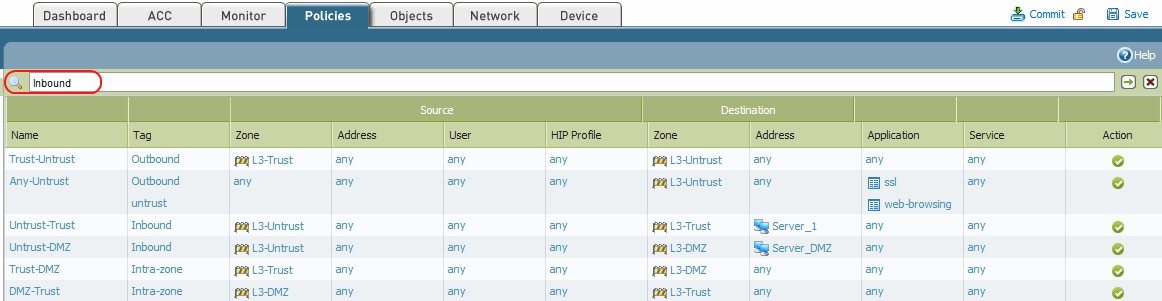 How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
How To Tag And Filter Security Policy Rules Knowledge Base Palo Alto Networks
Evaluation Order Of Panorama Pushed Security Policies Knowledge Base Palo Alto Networks
 Palo Alto Firewalls Policies And Rules Configuration And Concepts Youtube
Palo Alto Firewalls Policies And Rules Configuration And Concepts Youtube
Security Best Practices Checklist For Palo Alto Networks
 Palo Alto Firewall Initial Config Youtube
Palo Alto Firewall Initial Config Youtube
Optimize Your Security Policy Knowledge Base Palo Alto Networks
 Python Adding Firewall Rules To Palo Alto Using Pa Rest Api Cyruslab
Python Adding Firewall Rules To Palo Alto Using Pa Rest Api Cyruslab
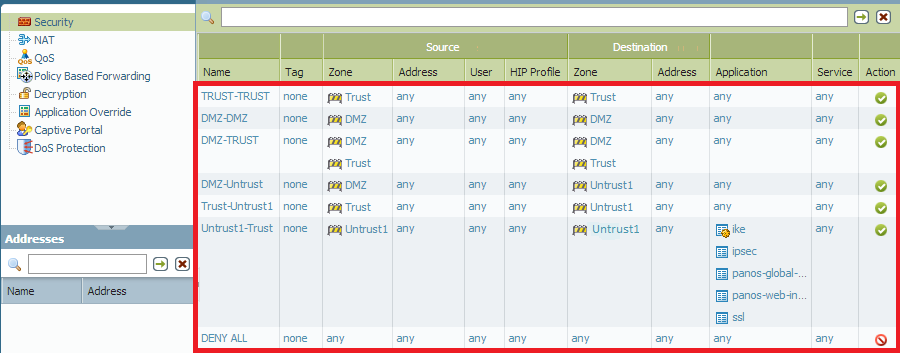 How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks
How To See Traffic From Default Security Policies In Traffic Lo Knowledge Base Palo Alto Networks
 Best Practice Training For Palo Alto Networks
Best Practice Training For Palo Alto Networks
Posting Komentar untuk "Palo Alto Firewall Best Practices"